Cyber fraud via email: How to recognize and defend against phishing
Cybercriminals are using increasingly sophisticated methods to obtain sensitive information. Two recent phishing attempts targeted Deutsche Kreditbank (DKB) and ING. In both cases, the fraudsters used deceptively genuine emails urging the recipient to take urgent action.
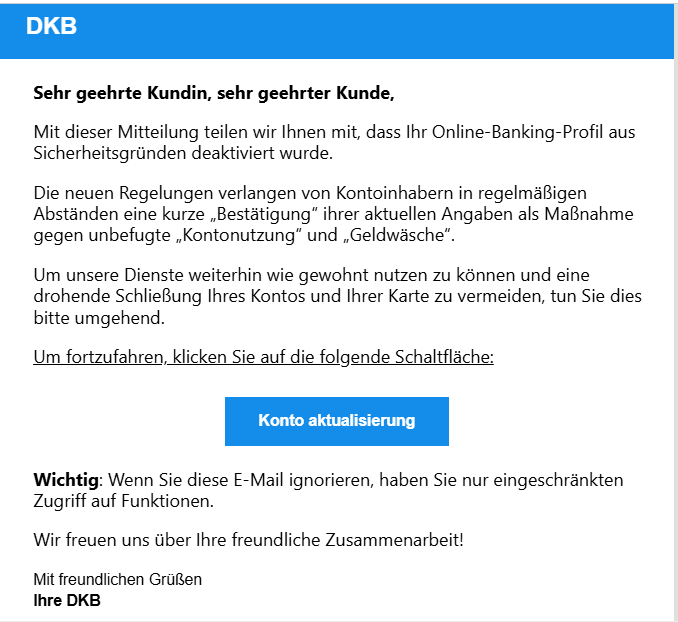
1. Fraudulent email on behalf of DKB (“new regulations”) – February 20, 2025
In this phishing email, recipients receive a warning that their online banking has been deactivated. The reasons given are “security reasons” and new alleged ‘regulations’ that require a “quick confirmation” of personal data. Particularly striking are phrases such as “unauthorized account use” and “money laundering,” which are intended to deliberately create fear and pressure. The message also threatens restricted functions or even account closure if the data is not confirmed “immediately.”
ATTENTION: Banks never ask you to confirm your login details by email.
2. Phishing attack on ING customers (“Account update required”) – February 19, 2025
Another fraudulent email claims that an ING account is inactive and needs to be reactivated. The recipient is asked to click on a button in order to continue “benefiting from banking services.” However, the content appears suspicious: the email refers to reactivation, updating, and an update—terms that are not used synonymously in the official banking environment. In addition, this email contains different font sizes and spelling errors such as “account update.”
ATTENTION: Professional banking communication is clear, error-free, and conducted via secure channels.

How can you recognize phishing emails?
Many phishing emails ask the target to open an attachment or click on a link. The attachment then contains malware which, once executed, can infect an entire company network.
Malicious links usually lead to websites that are infected with malicious software, also known as malware. Or to websites run by fraudsters that ask you to enter sensitive data (e.g., login details).
To prevent this from happening to you and your employees, you should first check any suspicious emails carefully and not blindly follow the instructions they contain.
Recognize these 5 warning signs
1. Incorrect web address in the clickable link
If the email contains a link that you are asked to click on, check where it leads before clicking:
- Simply move the mouse pointer over the name of the link.
- Your email program will then display the actual web address hidden behind it.
- This allows you to see whether the link address belongs to another website. If this is the case: BEWARE!
If the hyperlink in the email contains a spelling mistake, a transposed letter, or an incorrect domain extension, you should also be suspicious. To better disguise this, hackers often use very similar web addresses that look like the original at first glance, e.g., micro-soft.com instead of microsoft.com.
2. Email arrives unexpectedly or is unusual
Unexpected or unusual emails should raise suspicion. Check for the following anomalies:
- Does the email contain many spelling or grammatical errors?
- Is it very unusual for the sender (e.g., does it have a completely different writing style, or does the content not match the sender)?
- Does the email ask you to click on a link or attachment, but you have a strange feeling about it?
- Does the subject line not match the content of the message?
- Was the email sent to an unusual mix of people?
If any of these apply, then be vigilant. It is right for your alarm bells to ring.
3. Request for unusual actions
- If employees are asked in an email to do something they have never had to do before, this is also a warning sign. It is probably a phishing attempt.
- If the email asks you to disclose sensitive data or make a transfer (even if supposedly instructed by your boss), this is also a warning sign.
4. Pressure builds up in the mail
Pressure is exerted on the target by suggesting that the company will suffer financial damage if they do not immediately follow the instructions in the email.
For example, the supposed boss writes in the email that a deal with a partner abroad will fall through if the transfer is not made within the next hour.
5. Email contains a suspicious attachment or link
If the email contains an attachment, take a close look at it using the preview function:
- Does the attachment match the message?
- Does it make sense in terms of content?
- Is the file type potentially dangerous?
Also, stay “click safe” with links in emails and check them. Don’t just click on them, but make sure they are safe using the methods described in 1. Incorrect web address in the clickable link.
Interested in security awareness training?
Contact the i-data team
i-data GmbH
0531 180 59 300
Steintorwall 3, 38100 Braunschweig
